Cyber Threats Targeting Renewable Energy Infrastructure: The Silent Storm
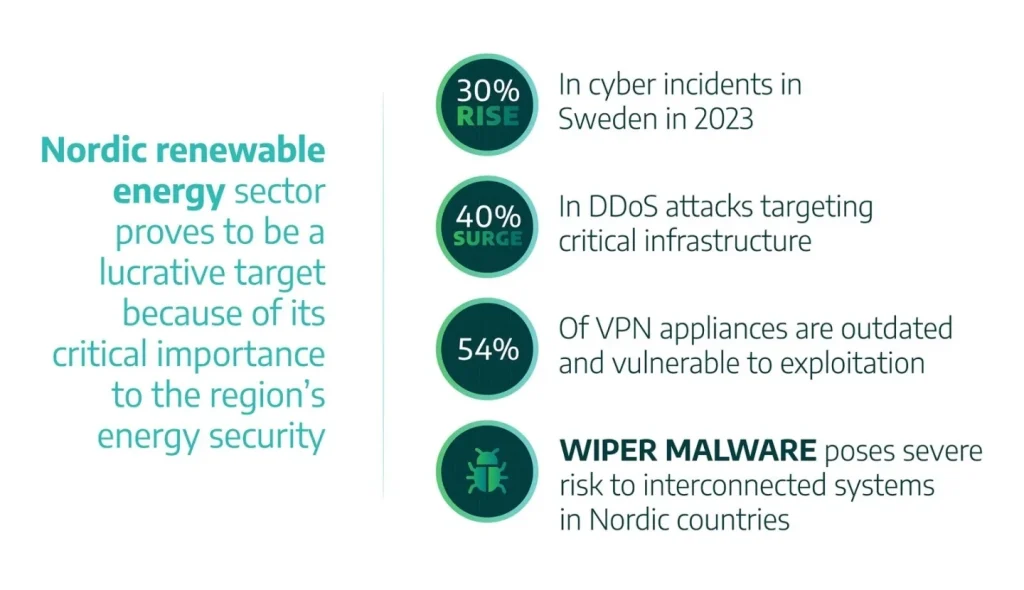
The race for a greener future is on. Wind turbines slice through the sky, solar panels blanket fields, and smart grids hum with digital intelligence. It’s a beautiful, necessary evolution. But here’s the thing no one talks about enough: this new, decentralized, and hyper-connected energy landscape is a cybersecurity nightmare waiting to happen.
Honestly, we’ve built a digital fortress with some surprisingly old, creaky doors. And hackers know it. Let’s dive into why renewable energy is so uniquely vulnerable and what’s at stake if we don’t shore up our defenses.
Why Renewables Are a Prime Target for Cyberattacks
It’s not just about the money anymore. Sure, ransomware is a huge motivator. But the threats against renewable energy infrastructure are more… strategic. We’re talking about nation-states aiming to destabilize a country, or hacktivists wanting to make a political point by literally turning off the lights.
The “New Grid” is a Complex Web
Traditional power plants were monolithic, walled-off systems. The modern renewable ecosystem? It’s a sprawling, interconnected web. Think about it: a single solar farm has thousands of panels, inverters, sensors, and communication links—all talking to each other. A wind farm has dozens of turbines, each a mini-computer perched 300 feet in the air. Every one of these connection points is a potential entry for a cyber threat.
Operational Technology (OT): The Achilles’ Heel
This is the big one. Operational Technology—the hardware and software that controls physical devices, like the systems that angle a solar panel or adjust a turbine’s blade pitch—was never designed with the internet in mind. It was built for reliability and safety, not to fend off Russian or Chinese hackers.
Well, now that OT is connected to corporate IT networks for efficiency and data analytics. And that connection, you know, creates a bridge. A bridge that allows a hacker who’s breached an office email system to eventually find their way into the system that controls the power flow from a hydroelectric dam. It’s a terrifying domino effect.
Common Cyber Threats in the Renewable Sector
The playbook against renewable energy infrastructure is growing. Here are the most common tactics:
- Ransomware: This is the digital extortion game. Hackers encrypt critical systems—like the software that manages an entire wind farm—and demand a ransom to restore access. The downtime isn’t just costly; it directly impacts energy production.
- Supply Chain Attacks: Imagine a hacker compromising the software of a major inverter manufacturer before it’s even installed in solar farms worldwide. That single vulnerability then gets baked into hundreds of critical energy assets. It’s a force multiplier for chaos.
- Data Integrity Attacks: This is insidious. Instead of just shutting things down, attackers subtly alter data. They might make a grid operator think there’s a massive power surplus, prompting them to curtail generation, or they could falsify performance data to cause millions in maintenance costs. You can’t fix a problem you don’t know exists.
- Phishing and Social Engineering: The human element is often the weakest link. A cleverly disguised email to an employee can be all it takes to get a foothold in the network.
Real-World Consequences: It’s Not Just Theory
This isn’t some futuristic scare tactic. The hits are already happening. In 2021, a ransomware attack forced a major U.S. solar and wind developer to shut down data centers and communication systems, crippling their ability to manage assets remotely. For days.
And let’s talk about the Colonial Pipeline attack for a second. While it was fossil fuel, it was a perfect, horrifying case study. The attack didn’t even hit the pipeline controls directly—it hit the business side. The result? Panic, fuel shortages, and a multi-state emergency. That same logic applies directly to renewables. A breach in one part of the system can cause cascading failure everywhere else.
Building a Cyber-Resilient Renewable Future
So, what’s the path forward? Throwing out technology isn’t an option. We need to get smarter, and fast. A robust cybersecurity strategy for renewable energy infrastructure isn’t a luxury; it’s as fundamental as the concrete in the foundation.
| Key Defense Pillars | What It Looks Like in Practice |
| Segmentation | Creating digital “air gaps” between IT and OT networks. A breach in accounting shouldn’t be able to reach the turbine controls. |
| Continuous Monitoring | Using AI and security tools to watch for unusual activity 24/7. Spotting the anomaly before it becomes a catastrophe. |
| Incident Response Planning | Having a clear, practiced playbook for when—not if—an attack happens. Who do you call? How do you isolate the problem? |
| Vendor Vetting | Demanding high cybersecurity standards from every supplier and manufacturer in your chain. |
| Workforce Training | Turning employees from a vulnerability into a first line of defense against phishing. |
It’s a constant cat-and-mouse game. The defenses we build today will be tested tomorrow. That means investing in people and processes, not just fancy software.
The Human Element in a Digital Battle
At the end of the day, cybersecurity isn’t just about firewalls and code. It’s about culture. It’s about the technician double-checking that a software update is legitimate. It’s about the executive prioritizing security budgets over slightly higher quarterly margins. It’s about understanding that the transition to clean energy must be a secure one.
We’re building the energy system of the next century. It’s a system that promises sustainability and independence. But that promise hinges on trust. Trust that when you flip the switch, the lights will come on. A successful cyberattack doesn’t just disrupt power; it shatters that trust and undermines the entire momentum of the green revolution.
The storm isn’t coming. It’s already on the horizon. The question is, how well will we weather it?







