Digital Marketing
How to Market to Digital Nomads: Reaching the Professionals Without an Address
Ecommerce
Localized Payment Method Implementation: The Secret Handshake for Global Ecommerce
Beyond the Box: How Personalization Algorithms Are Crafting Your Perfect Subscription
Beyond the Cart: How Augmented Reality Try-Ons Are Reshaping Fashion Ecommerce
Mobile
Cyber Security
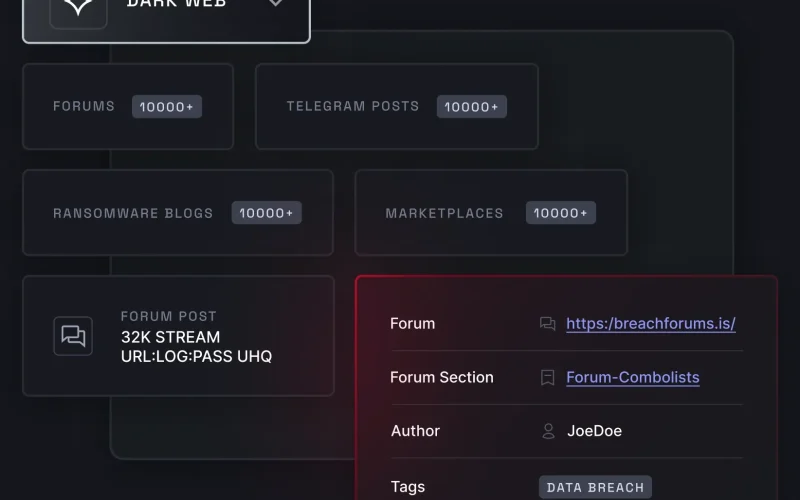
Dark Web Monitoring Strategies for Proactive Threat Intelligence
Let’s be honest—the dark web feels like a digital bogeyman. It’s this shadowy place where stolen data, leaked credentials, and hacker chatter swirl in the...
The Quantum Countdown: Navigating the Security Challenges of Post-Quantum Cryptography Adoption
Let's be honest. The conversation around quantum computing has shifted. It's no longer a distant "what if" from a sci-fi novel. It's a looming "when."...
Protecting Your Small Business from Deepfake Social Engineering Attacks
You know that gut feeling when something just seems… off? Maybe it’s an email from your boss asking for a weird wire transfer. Or a...
Cyber Threats Targeting Renewable Energy Infrastructure: The Silent Storm
The race for a greener future is on. Wind turbines slice through the sky, solar panels blanket fields, and smart grids hum with digital intelligence....
Your Face is the New Password: The Unseen Privacy Risks of Biometric Authentication
You unlock your phone with a glance. You pay for groceries with your thumbprint. It’s incredibly convenient, right? It feels like magic, a seamless blend...
Top Cybersecurity Threats of 2025 and How to Safeguard Against Them
Let’s face it—cybersecurity isn’t just about firewalls and antivirus anymore. By 2025, threats will be sneakier, faster, and way more personal. Here’s the deal: if...


 Dark Web Monitoring Strategies for Proactive Threat Intelligence
Dark Web Monitoring Strategies for Proactive Threat Intelligence  Beyond “Hey Google”: The Quiet Revolution of Ambient Computing in Your Smart Home
Beyond “Hey Google”: The Quiet Revolution of Ambient Computing in Your Smart Home  Localized Payment Method Implementation: The Secret Handshake for Global Ecommerce
Localized Payment Method Implementation: The Secret Handshake for Global Ecommerce  How to Market to Digital Nomads: Reaching the Professionals Without an Address
How to Market to Digital Nomads: Reaching the Professionals Without an Address  Voice Assistant Integration in Daily Mobile Workflows: Your Pocket-Sized Concierge
Voice Assistant Integration in Daily Mobile Workflows: Your Pocket-Sized Concierge